Before I get into the nuts and bolts, please familiarize yourself with: iPhone Jailbreak Videos: A Legal Primer and a How-To (Wired) as well as U.S. Declares iPhone Jailbreaking Legal, Over Apple’s Objections. Also bear in mind, while related, this is not about conducting penetration testing against iOS devices or applications on iOS. Now that you understand what you’re getting into, let’s get to it.
In my case, I upgraded to a newer phone and found my iPhone 3GS was just wasting away in a drawer. Having jailbroken it in the past, I figured I might as well get some use out of it and incorporate it into my tool chest. If you’ve never performed an iPhone jailbreak this might be a little tough to fully understand at first, but thankfully it has gotten a lot easier lately. Most jailbreaking these days can be performed with a single action, instead of jumping through hoops.
Check out the below links to get you started:
- Redsn0w
- Greenpois0n
- Cydia - App Store once jailbroken
Tip: To find the iOS version your device is running, plug it in to your computer and open iTunes, click your device and it should tell you the current version level.
In my case, I was running iOS 4.3.5 on my iPhone 3GS. Instead of taking time to find the right software to jailbreak it, I upgraded my phone to the latest iOS 5 version which the latest jailbreak software out there can handle no problem. Less than 5 minutes later my device had been released from Apple’s restrictions.
Once it booted back up, I launched Cydia (see above), a package manager/repository for utilities and applications. Take a look around and see what you can find, here’s a short list of what to look for:
- OpenSSH (great for manipulating the device remotely)
- Inetutils (ftp, inetd, ping, rlogin, telnet, tftp)
- Network-cmds (arp, ifconfig, netstat, route, traceroute)
- cURL / Wget
- Stealth MAC
- Stunnel
- tcpdump
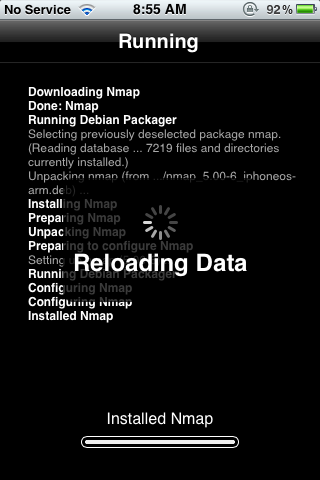
- NMAP
- MobileTerminal
- Ispeedtouched (wifi scanner + rainbow tables for WAP)
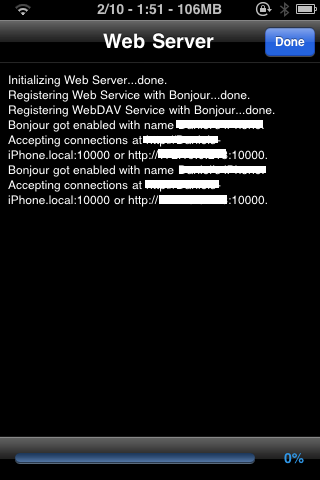
- iBrowser (temporary web server from your iPhone)
- iFile (browse contents of your device, also has web server capabilities)
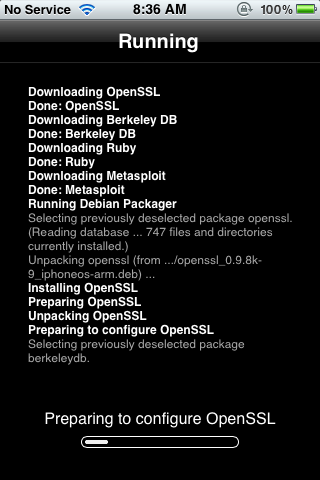
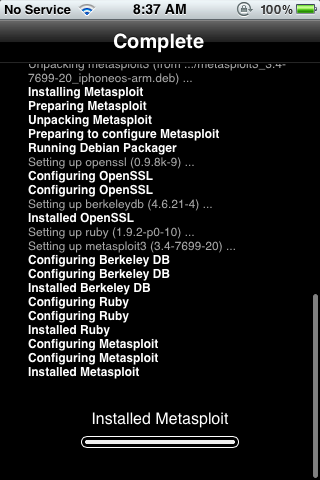
- metasploit (yup, you can put it on your phone)
Here’s a little bit of eye candy after the jailbreak was completed:


No comments:
Post a Comment