Without getting into the history of cryptography I will do my best to explain basic cryptography and how it works. Cryptography is essentially the science of mathematics using algorithms (or ciphers) to encrypt and decrypt plain text messages. An original message that you want to encrypt is known as plaintext. The message after it has been encrypted is known as ciphertext. In order to encrypt the original message, it must be processed by a mathematical algorithm that results in the ciphertext. Likewise, in order to decrypt the ciphertext, it must run through a mathematical algorithm to decrypt it back to the plaintext.
A very simple encryption algorithm is ROT13. The name of this method comes from the method of the algorithm. In order to encrypt the message, each character is rotated by 13 places, substituting the original letter by another letter 13 places down. ROT13 is an example of a simple Caesar cipher that was developed in ancient Rome.
Since ROT13 uses the 26 letters in the English alphabet, 26 = 2 x 13, ROT13 (rotate by 13 places) is it’s own inverse. So in order to decrypt a message encoded with ROT13, you just rotate the letters by another 13 places achieving the original plaintext message.
ROT13 character set
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz NOPQRSTUVWXYZABCDEFGHIJKLMnopqrstuvwxyzabcdefghijklm
To understand this better, take a look at the below table:
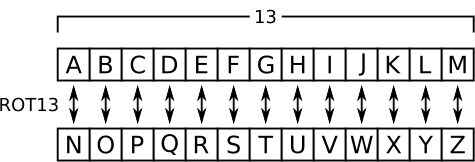
So, if I were to take the word, password and encode it with ROT13, we would be left withcnffjbeq
There are variants of ROT13, such as ROT47 which uses the 26 character alphabet, and also includes numbers and common symbols.
ROT47 character set
!"#$%&'()*+,-./0123456789:;< PQRSTUVWXYZ[\]^_`abcdefghijk
=>?@ABCDEFGHIJKLMN
lmnopqrstuvwxyz{|}
lmnopqrstuvwxyz{|}
What would our password be when encrypted by ROT47?
This concludes part 1 of Intro to Cryptography. In part 2 we will be diving into slightly more complicated cryptography and introduce a few new concepts. If there’s anything you want to see in this series, please leave a comment and let me know if you need help understanding anything I’m covering.
xEVD 7F? E@ =62C? 4CJAE@8C2A9JP
No comments:
Post a Comment