Last time I introduced cryptography, how it works, as well as some basic algorithms. I don’t want to spend too much time on the basics, as I figure that knowing what plaintext and ciphertext are should be good enough to get you started. Part 2 is going to focus on more advanced topics that may be complicated at first, but are generally easy to understand. Now that we understand what encryption is, we need to know that cryptography can be either strong or weak. To determine the strength of a type of encryption, we measure how long and how many resources it would take to break the encryption.
When reading about encryption elsewhere, you may have heard of bits, bytes and words. Measuring an encryption standard for strength is noted by the amount of cryptographic bits used to encrypt the data.
Here are a few more definitions you should get acquainted with:
Hashing: or the process of running data as an input through a hash function returns a fixed-size string, also known as the hash value.
Within cryptography, hash functions have the following basic requirements:
- Input can be of any length
- Output (the hash) has a fixed length
- Hashing is one way, collision-free and is easy to compute for any given x; where H(x).
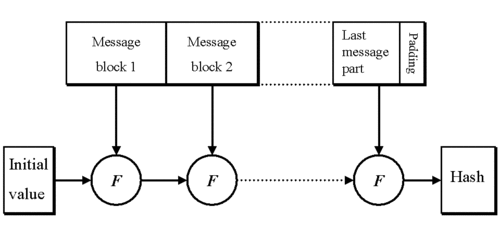
(where F = a compression function)
Common Hashes
Hashing algorithm Hash size MD5 16 bytes (128 bits) SHA-1 20 bytes (160 bits) SHA-256 32 bytes (256 bits) SHA-384 48 bytes (384 bits) SHA-512 64 bytes (512 bits)
Block ciphers
A type of symmetric encryption, rely on manipulating larger blocks of data (hence the name) during the encryption phase than stream ciphers. by design, block ciphers are inherently slower than stream ciphers.
Block ciphers work by taking a fixed-length block of plaintext and encrypting it into a block of ciphertext. These blocks are measured by their fixed length, or block size. Blocks are usually 64 bits in length, however, they will be increasing to 128 bits in the future.
The most commonly used block ciphers are DES and AES, the successor to DES.
Stream ciphers
Also a symmetric encryption algorithm that are much faster than block ciphers. During encryption, a stream cipher will generate a key or keystream using a specific sequence of bits. In order to encrypt the plaintext, the stream cipher will combine the keystream with the plaintext that is to be encrypted. This is usually done via bitwise XOR operations.
The most commonly used stream cipher today is RC4, also know as ARC4/ARCFOUR (Alleged RC4) or just “Rons Code” 4.
Padding
Two common methods of padding are bit and byte padding. Zero padding is also available. I won’t get into much details on it here, however, it is used in public key cryptography, such as OAEP with RSA.
This concludes part 2 of Intro to Cryptography. In part 3, I will go into XOR operations and the fundamentals and math behind the encryption. If there’s anything you want to see in this series, please leave a comment and let me know if you need help understanding anything I’m covering.
No comments:
Post a Comment